How Multi-Factor Authentication Works #
Multi-Factor Authentication (MFA) works on the principle of requiring users to provide two or more forms of identification before granting access to a system or application. These factors typically fall into three categories:
Something you know: This could be a password, PIN, or security question.
Something you have: Such as a physical token, a smartphone, or a smart card.
Something you are: This involves biometric verification like fingerprints, facial recognition, or iris scans.
By combining two or more of these factors, MFA significantly enhances security. Even if one factor is compromised, the other(s) provide an additional barrier to unauthorized access.
Implementation with RELIANOID ADC #
RELIANOID ADC (Application Delivery Controller) offers a seamless implementation of Multi-Factor Authentication (MFA) within HTTP applications, providing enhanced security without disrupting user experience. RELIANOID ADC’s implementation of MFA is transparent to any HTTP application, ensuring smooth integration and operation.
When an unauthorized user attempts to connect to an application, RELIANOID ADC intercepts the request and redirects the user to an internal portal located within the load balancer. This portal generates a secret token to the validated users session, which is included in the user’s request as a Cookie. This token serves as validation that the user has been authenticated through the MFA process.
After successful validation, the user is redirected back to the real application, thus completing the authentication process. RELIANOID ADC supports the use of multiple concatenated MFA portals, allowing for a more robust and layered security approach.
Use Case of Multi-Factor Authentication (MFA) #
Let’s delve into a specific use case showcasing how RELIANOID ADC seamlessly integrates Multi-Factor Authentication (MFA) to safeguard access to the protected web application, myapp.relianoid.com. This scenario outlines the step-by-step process a user undergoes when accessing the application, highlighting the effectiveness of MFA in bolstering security.
Phase 1: User Initiation #
An unauthorized user initiates the connection process by attempting to access the protected web application at myapp.relianoid.com using their web browser. They enter the URL: https://myapp.relianoid.com .
Phase 2: Load Balancer Detection #
RELIANOID ADC, configured with an HTTP Load Balancing (LSLB) farm and an HTTPS listener, intercepts the user’s request and identifies that the user is unauthenticated, triggering the MFA protocol.
Phase 3: Redirect to MFA Portal #
The load balancer redirects the user to a dedicated Multi-Factor Authentication (MFA) portal hosted at a specific URL, such as https://myapp.relianoid.com?mfa . Here, the user is presented with a login page prompting them to enter their credentials.
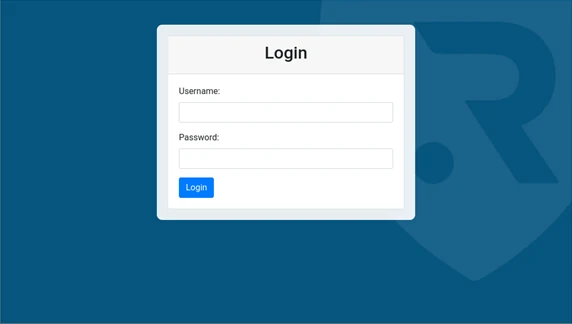
Phase 4: User Authentication #
The user proceeds to enter their credentials, typically comprising a username and password associated with their Active Directory account. RELIANOID ADC validates these credentials against the Active Directory connector configured within its settings.
Phase 5: MFA Token Generation #
Upon successful authentication, the MFA system delivers a token, signifying that the user has successfully passed the authentication process. This token is then securely provided to the user’s browser as an HTTP Cookie.
Phase 6: Redirect to Real Application #
Equipped with the generated token, the user is seamlessly redirected back to the original URL of the application, https://myapp.relianoid.com, indicating successful authentication.
Phase 7: Access to Real Application #
With authentication completed, the user gains unrestricted access to the real application. Depending on the application’s configuration, they may encounter an additional login screen specific to the application itself, or they may be granted direct access based on the MFA token provided.
External Applications for Token Generation #
To facilitate Multi-Factor Authentication (MFA), various external applications can be integrated with RELIANOID ADC to generate user tokens for validation. These applications typically utilize mobile devices or emails to provide users with additional authentication factors. Some popular applications for token generation include:
Google Authenticator: This mobile app generates time-based one-time passwords (TOTP) for MFA authentication.
Microsoft Authenticator: Similar to Google Authenticator, this app generates TOTP codes for MFA.
Duo Security: Duo offers a range of MFA methods, including push notifications, SMS passcodes, phone calls, and hardware tokens.
Authy: Authy is a cloud-based authentication service that offers TOTP codes, push notifications, and more for MFA.
These external applications provide users with flexibility and convenience while ensuring robust security through Multi-Factor Authentication.
RELIANOID ADC offers a seamless implementation within HTTP applications enhancing security while maintaining user experience.



