What is HTTP/2 Reset Attack? #
An HTTP/2 reset attack, also known as a “RST_STREAM” attack, is a type of cyber attack that targets the HTTP/2 protocol, which is used for web communication. In an HTTP/2 reset attack, an attacker sends malicious or specially crafted RST_STREAM frames to a web server in an attempt to disrupt or terminate a legitimate HTTP/2 connection between the server and a client (e.g., a web browser). The RST_STREAM frame is a part of the HTTP/2 protocol and is used to abruptly end an HTTP/2 stream.
By other hand, the HTTP/2 Rapid Reset Attack is a specific variation of the HTTP/2 reset attack that aims to create disruption and instability in HTTP/2 connections more quickly and efficiently. In this attack, an attacker sends a large number of RST_STREAM frames in rapid succession to a target server. The key characteristic of this attack is the speed at which RST_STREAM frames are sent, overwhelming the server’s processing capabilities and causing the server to terminate a significant number of HTTP/2 streams in a short amount of time.
How does HTTP/2 Reset Attack work? #
Usually, a HTT/2 Reset Attack behave as follows:
1. The attacker initiates an HTTP/2 connection with the target server.
2. During the connection, the attacker sends RST_STREAM frames with specific stream identifiers or other malicious parameters.
3. The server, upon receiving these RST_STREAM frames, abruptly terminates the associated HTTP/2 streams, resulting in disruption of the communication between the server and the client for those particular streams.
4. This disruption can lead to various undesirable consequences, such as incomplete page rendering, service interruptions, or potential resource exhaustion on the server side.
The goal of an HTTP/2 reset attack may vary. It could be used for causing service disruption, creating denial-of-service (DoS) conditions, or possibly exploiting vulnerabilities in the HTTP/2 stack on the server side. The attacker might use this method to exploit weaknesses in the server’s handling of RST_STREAM frames.
How to mitigate a HTTP/2 Reset Attack? #
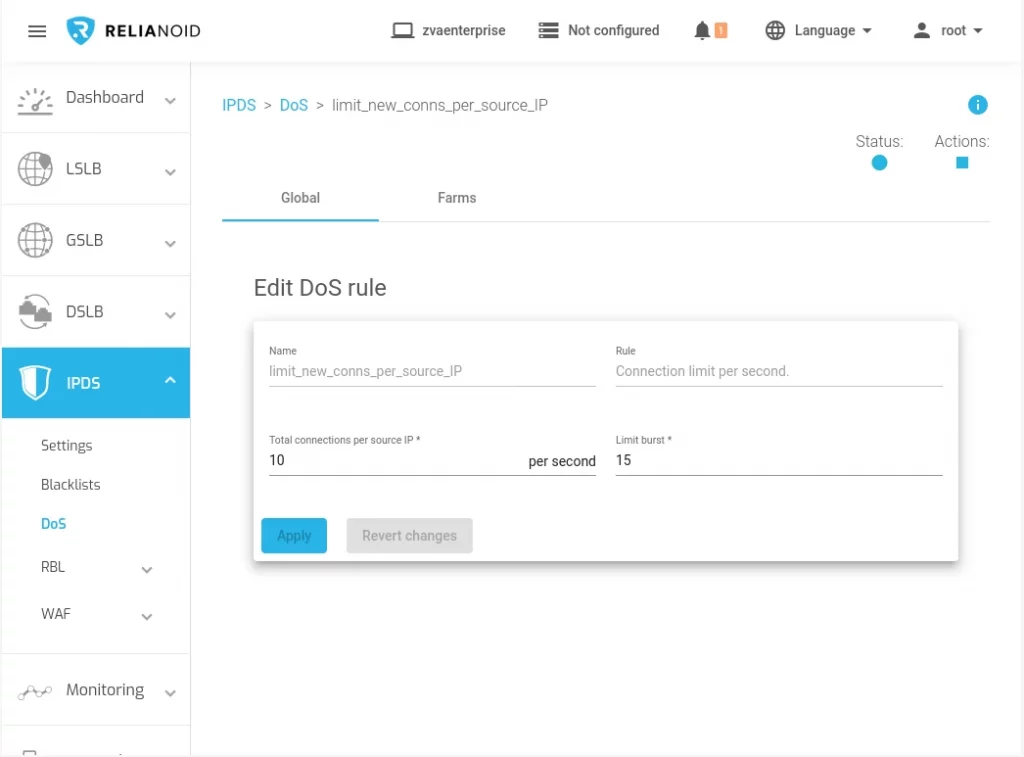
To mitigate HTTP/2 reset attacks, server administrators and developers should keep their HTTP/2 implementations up to date, employ security measures, and consider rate limiting and filtering of incoming HTTP/2 traffic to prevent or limit the impact of such attacks. Additionally, they should monitor their server’s behavior and logs for any unusual or suspicious activities.
With a Load Balancer with advanced security features, such as RELIANOID Load Balancer, you can make use of the DoS component included in the IPDS module for rate limiting of new connections per client.